
[Updated] Server security is one of the most fundamental issues in the field of information technology and requires a lot of expertise to implement security. Server security includes a range of topics: network security, operating system security, web services security, and their security configuration. In this article, all server security requirements, which are the basis of sites and information on the web, will be examined and concluded. We are also trying to learn you How to test security of VPS Server. You can visit the packages available in Eldernode to purchase a VPS Server.
Table of Contents
Tutorial test security of VPS Server
Currently, Linux vps server security and Windows server security are more discussed and used. These two operating systems have completely different structures and modes of operation and have something in common only in some cases. In a Linux server, a server with a minimal operating system is usually deliver, which, of course, is quite appropriate to the user’s need for web services. The centos operating system is most commonly used on Linux hosting servers, and the popular and powerful Cpanel and DirectAdmin control panels also support this Linux distribution.
How to test security of VPS Server
Due to the fact that in shared hosting services, a large number of sites are shared on a server and use shared space and resources, security should be given more attention. In the continuation of this article, join us to learn you How to test security of VPS.
Start working with the server
Given that the operating system we are using is Windows, communication with Linux servers is done by putty software and Windows servers with Remote Desktop Connection. According to the subject of this article, which is about security, after installing the operating system and services used on the server, you should do a few principles such as restricting services, disabling unusable services.
Server security configuration
Due to the fact that in the new era, security threats and ways of attack have taken on a new shape and are changing daily, security services in organizations and organs must also be updated in line with these changes. Information security services are a set of security services that cover a wide range of information and security needs of servers of companies and organizations.
The release of spyware and malware by internal and external agents or the leakage of vital information by these agents can be examples of these threats.
Penetration test
Penetration test is a systematic and planned method that checks the vulnerabilities and security holes of the server, network and resources and programs connected to it. This service, which is in the first category, simulates hacker attacks on the intended targets and after identifying security holes, provides appropriate solutions to secure them.
Types of penetration testing
1. Transparent test
2. Black box test
3. Gray box test
In the black box test, the tester has no prior information about the system and conducts the test. However, in the transparent test, the tester has complete specifications and comprehensive information about the system, based on which he performs a simulated attack, and in the gray box test, the tester has access to only some information and does not have comprehensive information.
Based on the sensitivity of the systems and their level of security, testing should be perform. If high security is required, a transparent test should be performed, and if the system and its security are less important, a gray box and a black box test will suffice. In fact, penetration testing should be done in a planned manner and with prior coordination with the owner of the system and can not be an uncoordinated action because some equipment or network system may have problems during the test.
Set up SIM
One of the key to maintaining an organization’s security is using products called SIM or Security Information Management. With the help of this software, we can get complete information about the events of a system in order to analyze them.
Security information management system is software that collects all the logs of different systems and reacts in case of system logs if it detects an unexpected behavior or a so-called Bad Behavior.
Set up IDS / IPS
Systems detect and prevent intrusion of traffic on the network in more detail than a firewall. Similar to antivirus systems, IDS and IPS tools monitor traffic and compare each packet with database of known attack specifications.
Once the pattern of attacks is detect, these tools take effect. IDS and IPS have many common features. In fact, most IPSs have an IDS at their core. The key difference between these technologies is that IDS tools detect network traffic to alert malicious users to an attack; But IPS tools go one step further and automatically block harmful traffic.
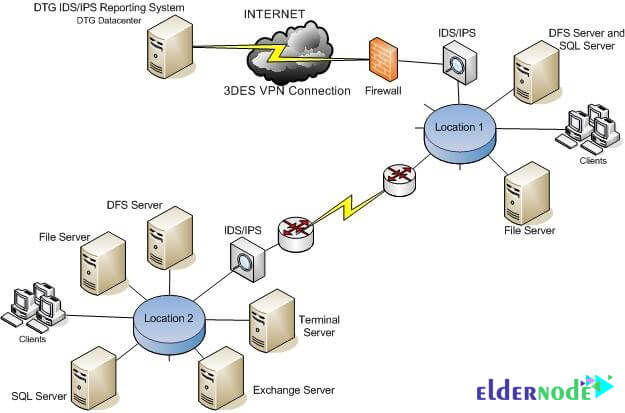
Note: Log monitoring system is software that is able to collect and report various system logs.
Firewall Installation
Setting up firewalls and UTMs Hardware and software UTMs in organizations and companies in the best and most secure way possible is one of the security needs of any organization.
Software firewalls are install on operating systems and control the incoming and outgoing traffic to the network or operating system. Such firewalls are mostly for home use and small and medium organizations and companies. Software firewalls for unauthorized access, trojans and malicious code, computer worms and more can protect systems.
Hardware firewalls are usually installing as infrastructure by manufacturers on hardware boards and usually operate as router on the network. A router can also operate on a network as a hardware firewall. By default, a hardware firewall can protect unwanted data and traffic from entering the network and information without making any initial adjustments.
Manage security holes
Update management software and security holes that save time, money and bandwidth for small and large networks and provide security reports for systems within the network and update them in the shortest possible time.
Web application security
Solutions and services for testing, scanning and fixing security holes in web applications with different technologies.
Security and risk advice
Consulting in the field of risk management and security of damaged systems after malware attacks and implementation and deployment of information security management system (ISMS) which is a management solution to create, implement and deploy, monitor and review and maintain and improve information security in the organization.
Prevent Simlink attacks
Preventing Simlink attacks is one of the most basic aspects of server management and security. By preventing Simlink attacks, the security of each user on the server will be account for, and its weakness will not have a negative effect on other accounts.
What is Simlink?
Simlink is a feature that allows you to create a reference from one file or directory to another. For example, the test.php file is located in the home/test path. If we want the test.php file to be visible, executable and even editable in another path, for example home/sample, we can use symlink. This feature is supporting on many operating systems, but their names and functions are different.
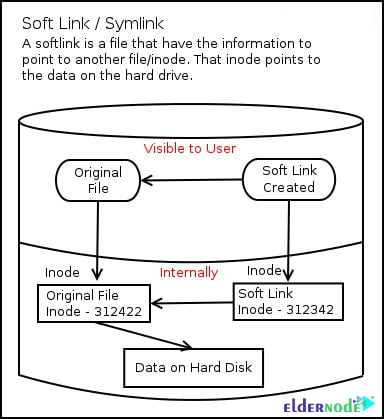
How to prevent Simlink in Cpanel
Preventing Simlink in Cpanel can be done in several steps and working methods. symlink is one of the most dangerous things to do on a server. Simlink is one of the core tools of the Linux operating system. If the problem and limitation of symlink in the Linux server is not resolved, if an account is compromised, symlink can be infiltrated to other accounts as well. The cloudlinux operating system has largely been able to resolve this issue. This operating system uses a tool called cagefs to lock each account in a cage in its domain.
To prevent symlink in Cpanel, do the following:
1. Go to Home » Service Configuration » Apache Configuration » Global Configuration in WHM.
Do the following on the page:
2. Set the Server Tokens value from the drop-down menu to ProductOnly.
3. Uncheck FollowSymLinks and ExecCGI in the Directory “/” Options. Make sure the SymLinksIfOwnerMatch check box is enabled.
4. Save items.
5. Go to Home » Service Configuration » PHP Configuration Editor and select Advanced Mode.
6. Find the disable_functions item and enter symlink and ln in its value in addition to the available values.
7. Save items.
8. Go to Home » Security Center » Apache mod_userdir Tweak and activate the Enable mod_userdir Protection check box and click Save.
9. Go to Home » Security Center » PHP open_basedir Tweak and check the Enable php open_basedir Protection check box and click Save.
10. Go to Home » Security Center » Shell Fork Bomb Protection and click on Enable Protection.
11. Use the suphp handler on the apache web server for php.
The above greatly limits the symlink operation but does not definitively disable it.
There are other things to limit symlink, some of which cause the service to malfunction, which are not covered here.
How to prevent Simlink in DirectAdmin
There are several ways to prevent Simlink in Direct Admin.
symlink is one of the most dangerous things to do on a server. Simlink is one of the core tools of the Linux operating system. If the problem and limitation of symlink in the Linux server is not resolved, if an account is compromised, symlink can be infiltrated to other accounts as well. The cloudlinux operating system has largely been able to resolve this issue. This operating system uses a tool called cagefs to lock each account in a cage in its domain.
To prevent symlink in DirectAdmin, do the following:
Enter the following commands in ssh. This command includes the security settings of Simlink.
cd /usr/local/directadmin/custombuild./build update./build set harden-symlinks-patch yes./build set secure_htaccess no./build apache./build rewrite_confsThen enter the following command to find the php.ini path in ssh:
/usr/local/bin/php -i | grep ‘Loaded Configuration File’Use the nano command to edit the file and find disable_functions. In addition to the values in the symlink, enter and save ln.
Conclusion
Penetration test is a systematic and planned process that checks the vulnerabilities and security holes of the server, network and resources and programs connected to it by simulating a hacker attack. In such a way that penetration testing can be controll and organize using internal sources such as host security system or external sources. Therefore, this test, which is a simulated attack, is using to find problems and measure the security of the server and the networks connected to it. This article explained how to test the security of VPS in full. You can refer to the article 20 Ways to Secure a Linux Virtual Server to Prevent Hacking if you wish.




