Nmap, short for Network Mapper, is a network discovery and security auditing tool. As an administrator, you need a network scanning tool that would be able to use IP packets to identify all the devices connected to a network. Nmap is a free and open-source network scanner and provides information on the services and operating systems they are running. Although Network mapper has been developed for enterprise-scale networks, it is also used by smaller companies. However, It is designed to rapidly scan large networks, but works fine against single hosts. This article is going to present the Introduction Nmap tool and check its applications. If you are preparing to purchase a fully managed Linux VPS, you can count on our technical team and order your considered package in Eldernode.
Table of Contents
Introduction Nmap Tool
Nmap is one of the most popular tools for network discovery that is released under the GPL license. To map your network, you can use Nmap and find live hosts on a network, perform port scanning, ping sweeps, OS detection, and version detection. Not only administrators, network admins, and penetration testers, but also malicious hackers use this free tool. Also, Nmap provides powerful scanning options since it is simple and easy to remember flags. Nmap is originally written for Linux, but it has been ported to major operating systems, such as Windows, Solaris, HP-UX, etc.
Nmap Applications
The program is available for many different operating systems such as Linux, Free BSD, and Gentoo. It is most commonly used via a command-line interface. Nmap is now used in many website monitoring tools to audit the traffic between web servers and IoT devices. Nmap is using in three core processes:
1- Nmap gives you detailed information on every IP active on your networks, and each IP can then be scanned. In this way, you can check whether an IP is being used by a legitimate service, or by an external attacker.
2- Nmap provides information on your network. You can use it and provide a list of live hosts and open ports, as well as identifying the OS of every connected device. So, you will have a valuable tool in ongoing system monitoring, as well as a critical part of pen-testing. You have learned about the Metasploit framework, then, you can use Nmap alongside it to probe and then repair network vulnerabilities.
3- You can use Nmap to scan your own web server (particularly if you are hosting your website from home) and it is simulating the process that a hacker would use to attack your site. So, if you are looking for a tool to protect personal and business websites, you will find this tool valuable. It helps you to use a powerful way of identifying security vulnerabilities by Attacking your own site.
How Does Nmap Work?
Nmap is an extremely powerful piece of software. You can use it easily and correctly if you try to have a good deal of background knowledge of this tool.
Nmap checks a network for hosts and services. software platform sends information hosts and services. Once it gets the response, will read and interprets it to use the information to create a map of the network. So, it will provide a map that includes detailed information on what each port is doing and who or what is using it, how the hosts are connecting, what is and is not making it through the firewall, and listing any security issues that come up.
Using a complex system of scripts that communicate with every part of the network, Nmap will be able to do all of the mentioned activities. Since the Nmap scripts are capable of vulnerability detection, backdoor detection, vulnerability exploitation, and network discovery, the scripts act as communication tools between the network components and their human users.
What Does Nmap scan?
As an administrator, you can use Nmap to scan for:
– Open ports and services
– Discover services along with their versions
– Guess the operating system running on a target machine
– Get accurate packet routes till the target machine
– Monitoring hosts
Nmap Scan Types
Using Nmap, allows you to use a variety of scans. Let’s review what scans can be performed by Nmap:
– TCP SCAN
– TCP SCAN
– SYN SCAN
– ACK SCAN
– FIN SCAN
– NULL SCAN
– XMAS SCAN
– RPC SCAN
– IDLE SCAN
Also, you can refer to Nmap Commands to learn more.
Nmap Features
To perform various activities like OS detection, finding open ports, and network vulnerabilities, Nmap uses NSE scripts. In spite of port scanning, Nmap offers many additional features. Let’s see them below:
– Host discovery
– Operating system detection
– Service version detection
– Network information about targets, such as DNS names, device types, and MAC addresses
– Ability to scan for well-known vulnerabilities.
Nmap Advantages
Nmap is known as the best hacking tool. Here are some advantages that users have reported to encourage others to start using that:
– Built-in scripts allow for vulnerability testing
– Enumeration
– Port Scanning
– Vulnerability checks
– Network scans
– Vulnerability checks
– Open/Closed ports.
– OS detection
– Easily scripted and analyzed
– IDs hosts
– Checking firewall rules
– User community support is ubiquitous
– Highly accurate endpoint identification
– The unique process of fingerprinting applications/devices
– NMap is easy to use and highly configurable
Nmap Disadvantages
Some users say it is hard to mention anything but as usual, let’s see what are the dark points of this popular tool:
– Modules are not fast enough
– It is hard for new people to use it as there are too many switches
– CLI only, web-based version would be something the developers would consider.
– Not supported by a vendor
– You cannot use this tool if there is no network, depending on the network and the security on it.
– Nmap scripts are written in Lua, which is not a mainstream language.
How to use Nmap?
Previously, you learned How To Install Nmap on Linux. However, to start using Nmap, you need to be familiar with command-line interfaces. Not for basic network monitoring, but if you need to go for advance using, you should be able to write scripts to automate common tasks.
Zenmap is the official Nmap Security Scanner GUI. Zenmap interface is very intuitive. When you launch Zenmap from the graphical interface, you will find the option to run it as a root.
Note: For Windows, Nmap comes with a custom installer (namp<version>setup.exe). So, you can download and run this installer, and it automatically configures Nmap on your system.
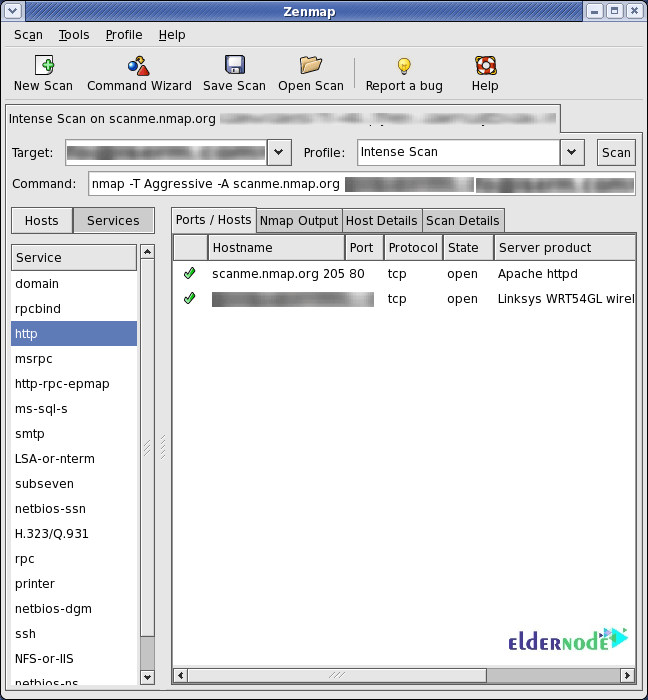
In addition, as a system admin, you will be able to use Nmap easily since you are familiar with most of the tools it provides. Nmap brings a wide range of these tools into one program. So, it will not force you to skip between separate and discrete network monitoring tools. Once you install Nmap, the below abilities are ready to be used:
– Run a Ping Scan
– Run A Host Scan
– Use Nmap in Kali Linux
Most of the common functions of Nmap can be executed using a single command, and the program also uses a number of ‘shortcut’ commands that can be used to automate common tasks. Here is common Nmap functions:
– Ping Scanning
– port Scanning
– Host Scanning
– OS Scanning
– Output to Files
– Scan top Ports
– Disable DNS Resolution
Conclusion
In this article, Nmap was introduced to you and you reviewed all its applications. Nmap is used to provide detailed, real-time information on your networks, and on the devices connected to them. From now on, you have a solution to the problem of identifying activity on a network as it scans the entire system and makes a map of every part of it. Nmap is legal if used properly since it helps you to protect your network from hackers. Nmap is used for Internet security companies since it is ideal for scanning a system and understand what weaknesses exist that a hacker could potentially exploit.