
[Updated] Each device on a network has an IP. There are two types of IPs: public and private. Public IP addresses are available anywhere in the world. But private types are used in internal networks. Such as 192.168x.x, or 10.0x.x. In order to receive information from the Internet, data requests are exchanged with either a public IP address owned by the router or a private IP address corresponding to the address of the computer or any other device connected to the network. SSH forwarding is useful for transporting network data of services that use an unencrypted protocol. In this article, you will learn How To Create an SSH Tunnel or Port Forward in Linux. Visiting various packages of Eldernode will fulfill your expectations to buy your own Linux VPS.
Table of Contents
What Is SSH Port Forwarding?
SSH tunneling or SSH port forwarding is quite simply able to route internal network traffic to remote hosts through SSH tunnels. This means that all incoming traffic is secured through encryption. This solution provides a simple way to create a VPN tunnel that is a practical way to connect to private networks over the Internet. It may also use the Internet platform to access servers located behind NAT or firewalls. SSH sessions allow tunneling of all network communications by default. There are currently three methods for SSH port forwarding: Local, Remote, and Dynamic. Normally we can securely connect to our server using SSH.
Tutorial Setup SSH Tunneling Or SSH port Forwarding In Linux
The SSH Tunnel (also known as SSH port forwarding) is actually the easy routing of local network traffic via SSH to remote hosts. This way all your connections are secure using encryption. This provides an easy way to define a VPN (Virtual Private Network), which connects to private networks through insecure public networks such as the Internet. You may also access the local servers behind NAT and Firewall from a secure tunnel platform, as implemented in ngrok.
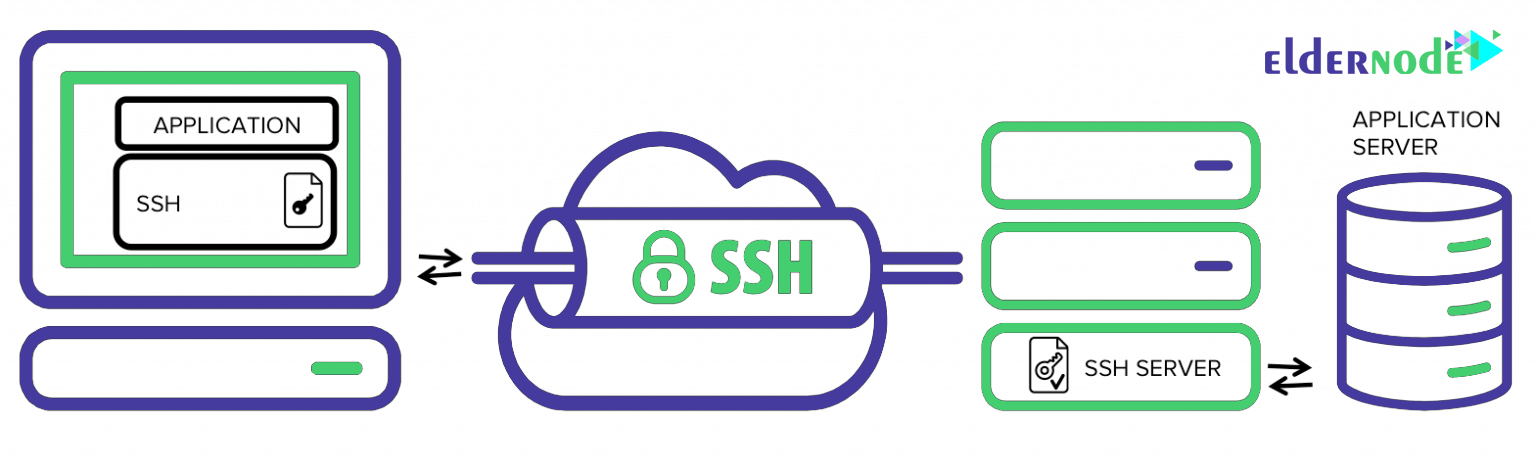
By default, SSH sessions allow tunneling for network communication. There are also three types of SSH port forwarding:
1- Local
2- Dynamic
3- Remote
We continue this example with respect to the default values below:
Local Host: YourIPAddress
Remote host: server1.example.com
You can securely connect to a remote server using SSH as in the example below. I have configured the ssh login without a password between remote and local hosts, so I am not asked for a password.
ssh [email protected]Local SSH Port Forwarding
This type of port forwarding allows you to connect to a remote server from your local computer. Suppose you are behind a restricted firewall or are blocked by an output firewall from accessing an application running on port 3000 on your remote server. You can forward a local port (for example 8080) that you can use to access the application locally.
Note: The -L option is for defining the forwarded port to the remote host and remote port.
ssh [email protected] -L 8080: server1.example.com:3000Adding the -N option means not executing a remote command, in which case you will not receive a shell.
ssh -N [email protected] -L 8080: server1.example.com:3000The -f option executes the ssh command in the background environment.
Now open a browser on your local machine instead of accessing the remote app. Instead of using server1.example.com:3000, you can easily use localhost: 8080 or YouIPAddress: 8080 as shown below:

Remote SSH Port Forwarding
Remote SSH Port Forwarding allows you to connect to your local computer from your remote machine.
Note: By default, ssh does not allow remote port forwarding. You can enable it using the GatewayPorts section in the main sshd settings located in the etc/ssh/sshd_config/ config file on your remote host.
Open the file and edit it using your favorite text editor:
sudo vim /etc/ssh/sshd_configLook for the desired section and remove it from the comment and set its value as yes as below:
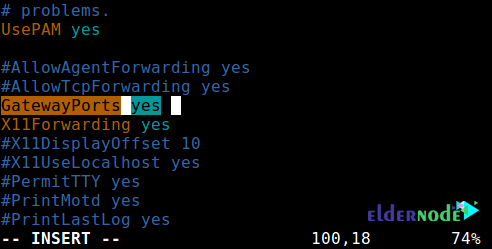
Save the changes and exit. Then in order to apply the changes you need to restart the sshd service:
sudo systemctl restart sshdOR
sudo service sshd restartThen, run the following command to forward port 5000 on the remote machine to port 3000 on the local machine:
ssh -f -N [email protected] -R 5000:localhost:3000Once you understand this method of tunneling, you can easily and securely publish a local programming server, especially if it is behind NAT and Firewall.
Tunnels like Ngrok, pagekite, localtunnel, and countless other methods all work the same way.
Dynamic SSH Port Forwarding
This is the third method of port forwarding. Unlike local port forward and remote, which made it possible to communicate with a separate port, this method allows for a full range of TCP communications through a range of ports.
The Dynamic Port Forwarding method sets up and defines your machine as a SOCKS proxy server that is playing by default on port 1080.
For starters, SOCKS is an Internet protocol that defines how a client connects to a server through a proxy server (here SSH). You can enable Dynamic Port Forwarding with the -D option.
The following command starts a SOCKS proxy on port 1080 that allows you to connect to a remote host.
ssh -f -N -D 1080 [email protected]From now on, you can make applications on your machine use this SSH Proxy server. All you have to do is configure them to use this server.
Note that Socks Proxy will stop working after session ssh is closed.
Conclusion
In this article, we have explained the different types of port forwarding from one machine to another and tunneling traffic through a secure SSH connection. This is one of the many uses of SSH. Port forwarding ssh has significant drawbacks, this command can have adverse effects. Can be used to bypass network monitoring and traffic filtering (or firewall) applications. Hackers can use it for their malicious activities. If you are interested in learning more, find our articles on Setup SSH Tunnel With Putty and Port Forwarding On Mikrotik.





What should I do to synchronize two files on two different Linux systems?
The rsync command is used for backups in Linux. It also has the ability to synchronize two files, these two files can be on one computer or another on a remote computer.
What is Bacula service for Linux and what does it do?
Bacula is a powerful software to set up a Backup Server for Windows and Linux networks. Its convenient feature is that it is multi-platform.
What is job scheduling in Linux?
Sometimes certain tasks need to be done periodically, such as backing up databases, sending emails and newsletters, and things like that. Schedule Task is used to do this in Windows. In open source operating systems such as Linux and Unix, there are tools called Cron and at that are used for this purpose.
What is the difference between SSH and Telnet?
SSH, which stands for Secure Shell, and Telnet, which stands for TeleNetwork, are two network protocols known for managing network equipment and remote servers. Using these tools, you can easily make configurations related to the mentioned devices through the command line they provide. The two tools are practically no different from each other, and you can do anything you can with SSH using Telnet, but the most important difference is the security issue. Telnet has no security mechanism
What is Shell?
The shell acts as the interface between the user and the kernel. shell is a useful program that receives commands and instructions from the user and delivers them to kernel for execution after translation.