Introducing Man in the Middle Attack. Hacker attacks on the Internet are being carried out with various methods. Among these, attacks such as Bruteforce and Man in the Middle are the most popular and, of course, the most dangerous attacks.
In this tutorial, we are going to introduce you to Man in the Middle attack. Stay with us.
ElderNode VPS hosting packages
Introducing Man in the middle attack
Man in the middle attack, known as MIM, MitM and MITMA in the world. It is one of the most dangerous types of hacker attacks.
This type of attack can be performed in layer 2 and layer 3 in the network. In this type of attack, the hacker puts himself between the connection of two nodes in the network and stores all the information and shows it to the hacker by passing information between two systems or servers in the network.
These attacks are a powerful eavesdropping on everything that happens on your network.
This attack is very dangerous because it does not involve users and administrators like other attacks, and like viruses, ransomware, backdoor, etc., it is not identifiable and easily captures information.
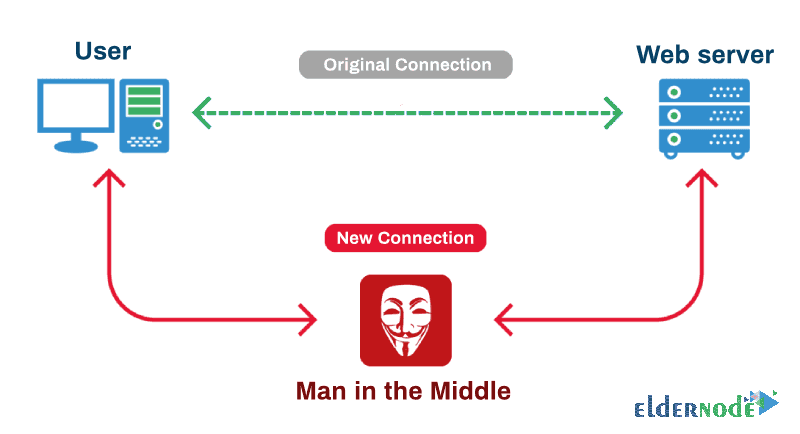
The image below shows the Man in the Middle attacks.
Man in the middle attack in layer 2
The MitM attack in Layer 2 is such that the attacker, by forging the MAC address on the network, leads the systems to believe that the Gateway has been transmitted.
The systems believe that they send all the packets to the hacker. In the same way the hacker sends the packets to the destination by copying all the entered information.
This process happens so fast that users are not aware of it, as if they are working on their network without interruption.
Note: This type of attack, also known as ARP Poisoning, can be thwarted with techniques such as DAI on smart switches.
Man in the Middle attack in Layer 3
MitM attack in layer 3 is much more common and of course more dangerous. In a Layer 2 attack, the hacker must have access to the physical layer of the network. Or capture a system on the network and launch the attack with various software. In layer 3, this type of attack can also be done remotely.
A Man in the Middle attack in Layer 3 can be between a web server and a user. It can also be between a virtual server and a user. In general, it will be able to control this attack with various methods.
This attack in Layer 3 is similar to the attack in Layer 2, except that in Layer 3, the attacker replaces itself with a router and moves and copies Layer 3 packets between the two systems.
In this type of attack, a hacker can easily obtain and copy passwords, entered commands, bank and system accounts, and everything you enter into your system.
For this reason, it is recommended to use secure and encrypted protocols to prevent this type of attack as much as possible.
For example, if you have a simple website, you enter your username and password when you log in to your admin area. The same way you enter (meaning Clear Text) is visible to the hacker. If you have a security certificate on your website, all your information will be encrypted. So the hacker will see meaningless and encrypted characters.
This way, it will not be able to use your passwords and other information easily.
Using security certification is very common and you will be able to use this system for most of your services.
Goodluck.




