The most reliable type of port scan is TCP, TCP Connect Scan, or Full Open Scan, sometimes known as Vanilla Scan. In this type of port scanning technique, the scanner sends a request to communicate with the destination server on the desired port. This request is sent by the TCP Connect scanner system. If the target server is in the requested port in Listening mode, the TCP Connect command will be successful. This means that the port is open, otherwise, the port is not available and no service is providing. In this article, we are going to teach you How to Scan ports using Connect Scan on Nmap. You can visit the packages available in Eldernode if you wish to purchase a VPS server.
Table of Contents
Tutorial Scan ports using Connect Scan on Nmap
Port scanning is a method using to check ports or open network ports. The port scanning process requires exploring each port on a host and identifying which ports are open. This process of scanning the port usually provides more valuable information about the host and system vulnerabilities from the ping.
Service identification is the next step in scanning methodology, which is usually doing using the same port scanning tools. By identifying open ports, a hacker can usually detect services associated with that port number.
In the continuation of this article, join us to teach you How to Scan ports using Connect Scan on Nmap.
Status of the ports on Nmap
Nmap is a free open-source tool that quickly and efficiently performs ping, port scanning, service detection, IP detection, and operating system detection. Nmap can scan a large number of machines in one session and is supported by many operating systems including Unix, Windows, and Linux. The status of the ports in the Nmap tool is determining in three modes. 1. Filtered, 2. Unfiltered, and 3. Open.
An open port means that the target machine accepts incoming requests from that port.
A filtered port means that a firewall or a network filter screens the port and prevents the port from being detected by tools such as Nmap.
Unfiltered port means that the port is specified as closed and no firewall or filter interferes with Nmap requests.
What is Connect Scan?
Connect scan is the default TCP scan type when SYN scan is not an option. This is the case when a user does not have raw packet privileges or is scanning IPv6 networks. In the Connect scan, Instead of writing raw packets as most other scan types do, Nmap asks the underlying operating system to establish a connection with the target machine and port by issuing the connect system call.
Note: This is the same high-level system call that web browsers, P2P clients, and most network-enabled applications use to communicate.
Connect scan is part of a programming interface known as the Berkeley Sockets API. This type of scan in Nmap works in such a way that instead of reading raw packet responses over the wire, it uses it to obtain status information about each connection.
In the Nmap TCP Connect scan, Nmap asks its main operating network to communicate with the target server by issuing a “Connect” system call. But the problem with this scan is that it takes time to do and more packets are needing to generate information. Targets, on the other hand, are more likely to connect because they try to communicate with the target of the same network-enabled applications as web browsers.
Scan ports using Connect Scan on Nmap step by step
Nmap is a free, open-source network scanner developed by Gordon Lyon. This scanner is using to detect hosts and services on a computer network by sending packets and analyzing responses. Nmap provides a number of features for exploring computer networks, including host and service discovery and operating system detection. Here we are going to teach you to step by step how to scan ports using Connect Scan on Nmap.
Scanning ports using Connect Scan is very easy. Just enter the following command.
Note: In the following command, instead of scanme.nmap.org, you should type the IP you want.
Nmap -sT scanme.nmap.orgThe output of the above command will be as follows:
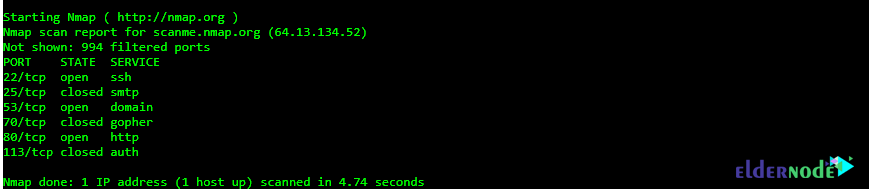
As you can see in the output above, ports 22, 53, and 80 are open. But ports 25, 70, and 113 are closed.
Conclusion
In this article, we tried to teach you How to Scan ports using Connect Scan on Nmap. Disadvantages of this type of scan include its ease of detection and filtering. Due to the fact that in this type of port scan, the TCP Handshake process is officially completed and the session is established and then disconnected, all sessions are logged in the firewall and can be traced. This can lead to the identification and prosecution of the attacker. But on the other hand, due to the fact that the accuracy of this type of scan is very high, a special account can be opened on it for legal scanning processes. It should note that this type of scan can use on any operating system.




