JSQL Injection is a powerful tool used for detecting and exploiting SQL injection vulnerabilities in web applications. By simulating various attack techniques, JSQL Injection helps developers identify and fix security loopholes in their code. In this article, we will guide you through the step-by-step process of installing JSQL Injection on Kali Linux. We have offered various packages on the Eldernode website for you to visit and purchase a Linux VPS server.
Table of Contents
Understanding the Basics of SQL Injection
SQL Injection is a common web application vulnerability. It occurs when an attacker exploits vulnerabilities in a web application’s input fields to insert malicious SQL statements into the application’s database query. The vulnerability arises when the application does not properly validate or sanitize user input before using it in SQL queries. As a result, the attacker can execute arbitrary SQL commands and potentially gain unauthorized access to the database.
What is JSQL Injection?
JSQL Injection is a powerful tool designed specifically for detecting and exploiting SQL injection vulnerabilities in web applications. It provides security professionals with a comprehensive solution for identifying potential vulnerabilities and strengthening the security of their applications. This tool offers a command-line interface that allows users to interact with the tool and perform various tasks related to SQL injection testing.

Advantages of Using JSQL Injection
Using JSQL Injection for SQL injection testing offers several advantages:
Efficiency
JSQL Injection automates the process of identifying SQL injection vulnerabilities, saving time and effort for security professionals. It performs automated tests and provides detailed reports on any vulnerabilities found.
Comprehensive Testing
JSQL Injection supports various types of SQL injection attacks, including union-based, blind-based, and time-based attacks. It covers a wide range of scenarios, ensuring thorough testing and identification of vulnerabilities.
Data Extraction
JSQL Injection allows security professionals to extract data from vulnerable databases easily. This can be useful for understanding the extent of the vulnerability and the potential impact of an attack.
Customization
JSQL Injection offers flexibility and customization options. Users can configure various settings, such as the number of concurrent threads, HTTP headers, and cookies, to adapt the tool to their specific testing needs.
Educational Tool
JSQL Injection can also serve as an educational tool for developers and security professionals to understand the impact of SQL injection vulnerabilities. By simulating attacks and demonstrating the consequences, it raises awareness about the importance of secure coding practices.
Installing Kali Linux
If you’re interested in installing Kali Linux on your operating system, you can refer to my previous articles for detailed instructions. They cover the step-by-step process of installing Kali Linux on VMware Workstation, VMware ESXi, and MacOS, providing you with the necessary guidance to set up your environment and explore the powerful tools and resources offered by Kali Linux. To learn more, check out the section on installing Kali Linux in my previous articles:
How to Install & Setup Kali Linux on VMware ESXi
How to Install & Setup Kali Linux on VMware Workstation
Tutorial Install Kali Linux on MacOS

Installing JSQL Injection on Kali Linux
First Update the System Repositories using the command below:
sudo apt updateThen run the following command to Install JSQL Injection:
sudo apt install jsql-injectionAfter the installation is complete, you can use the tools of JSQL as follows:
Configuring JSQL Injection
Once you have downloaded JSQL Injection, you need to configure it. To do this, follow these steps:
Open a terminal window and change to the JSQL Injection directory:
cd ~/Downloads/jsql-injectionCompile the JSQL Injection source code by running the following command:
javac -cp lib/*:. JSQLInjection/*.javaRun JSQL Injection by executing the following command:
jsql-injection -hJSQL Injection will start, and you will see the command line interface.
You can use JSQL by running the command below:
jsql -hHere is the JSQL Injection environment:
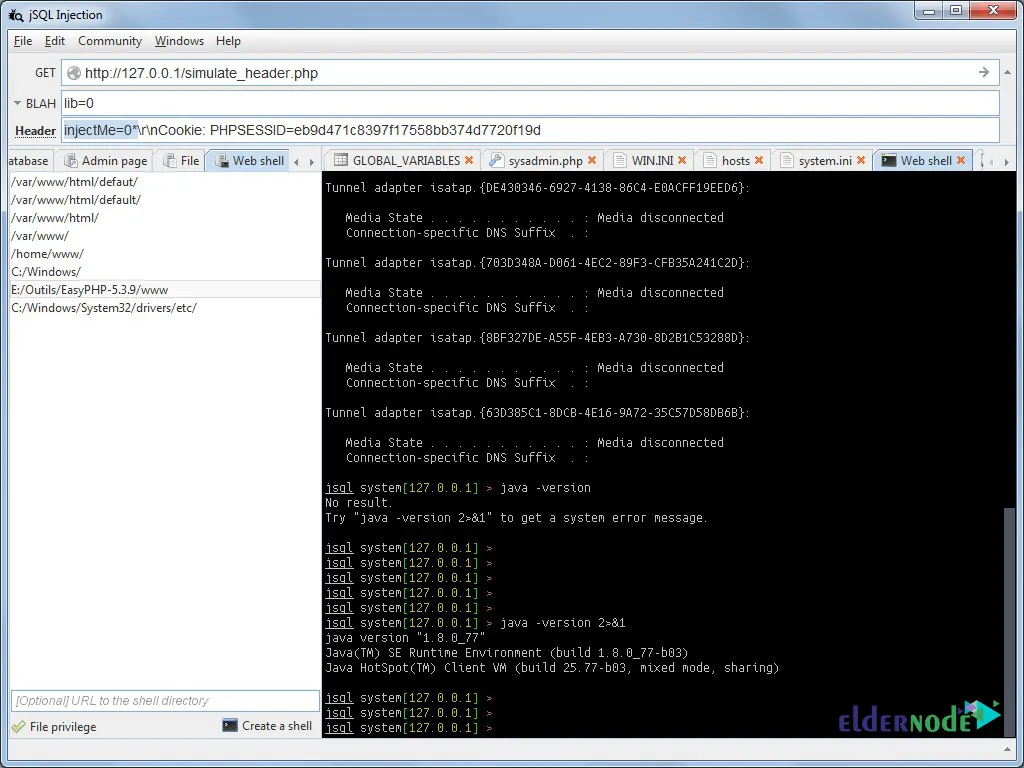
Conducting a JSQL Injection Attack
Conducting a JSQL Injection attack involves a series of steps aimed at exploiting SQL injection vulnerabilities in web applications. In fact, these attacks can lead to unauthorized access and data breaches, making it crucial to understand the process involved. However, it’s important to note that conducting such attacks without proper authorization is illegal and unethical. The steps typically involved in a JSQL Injection attack include identifying the target application, finding potential injection points, testing for vulnerability, analyzing the application’s response, extracting data, and potentially expanding the attack. Also, it is essential to prioritize web application security and prevent JSQL injection vulnerabilities to protect against such attacks.
Preventing JSQL Injection Attacks
Preventing JSQL Injection attacks is vital for maintaining the security and integrity of web applications. In fact, implementing preventive measures significantly reduces the risk of JSQL injection vulnerabilities. These measures include input validation and the use of parameterized queries, following the least privilege principle, ensuring strict error handling, utilizing web application firewalls (WAF), conducting regular security assessments, keeping software updated, and providing security awareness and training to developers and system administrators. Taking a proactive and layered approach to web application security helps mitigate the risk of SQL injection vulnerabilities and safeguards against potential attacks.
Conclusion and Final Thoughts
JSQL Injection is a valuable tool for security professionals involved in web application testing. Its automation capabilities, comprehensive testing features, and customization options make it an effective solution for detecting and mitigating SQL injection vulnerabilities. In this article, you learned How to Install JSQL Injection on Kali Linux and reviewed different tools of JSQL. By utilizing JSQL Injection, organizations can enhance the security of their web applications and protect sensitive data from unauthorized access.