
Proper firewall configuration is one of the most important aspects of system security. By default, Ubuntu comes with a firewall configuration tool called UFW (Uncomplicated Firewall). UFW is a user-friendly shelter for managing iptables firewall rules and its main purpose is to manage or easily manage iptables. In this article, we are going to teach you How to Limit SSH with UFW on Ubuntu 20.04. You can visit the packages available in Eldernode if you wish to purchase an Ubuntu VPS server.
Table of Contents
How to Limit SSH with UFW on Ubuntu 20.04
How to Syntax to limit SSH connections with UFW
In this section, we want to teach you how to Syntax to limit SSH (TCP port 22) connections with UFW. Note that the syntax is very simple. To do this you can see the following commands:
## ufw limit ssh various usage ##ufw limit sshufw limit ssh/tcpufw limit ssh comment 'Rate limit for openssh server'### if sshd is running on tcp port 2022 add ####ufw limit 2022/tcp comment 'SSH port rate limit'Limit SSH with UFW on Ubuntu 20.04 | Ubuntu 21.04
In the previous section, we mentioned some things about Syntax to limit SSH connections with UFW. Note that these rules are useful for protecting against brute-force logging attacks.
Now in this section, we want to discuss how to Limit SSH with UFW on Ubuntu 20.04. Note that when a restricted rule is used, UFW normally allows the connection. But if an IP address tries to make multiple connections in 30 seconds, it rejects the connection. Therefore, you need to confirm it after setup with the following commands:
sudo ufw limit ssh/tcp comment 'Rate limit for openssh serer'sudo ufw statusIt is interesting to know that the real rules in Iptables are as follows:
-A ufw-user-input -p tcp -m tcp --dport 22 -m conntrack --ctstate NEW -m recent --set --name DEFAULT --mask 255.255.255.255 --rsource-A ufw-user-input -p tcp -m tcp --dport 22 -m conntrack --ctstate NEW -m recent --update --seconds 30 --hitcount 6 --name DEFAULT --mask 255.255.255.255 --rsource -j ufw-user-limit-A ufw-user-input -p tcp -m tcp --dport 22 -j ufw-user-limit-acceptHow to Limit SSH with UFW and other protocols
In this section, we want to show you how Limiting ssh with UFW and other protocols. You can use the following commands to do this. You can use these commands to restrict other services as well:
ufw limit {service}## be careful with http/https limits as many users might be behind a large proxy server ##ufw limit 25/tcpufw limit httpufwufw limit httpsHow to Limit SSH using the GUFW GUI tool
In this section, we want to deal with Limiting ssh using the GUFW GUI tool. To do this, you must follow the steps below in order.
First, you need to make sure GUFW is installed on Ubuntu Linux. You can use the following command to perform this test:
sudo apt install gufwYou can now start by executing the following command:
gufw &It should be noted that authentication is required to run the GUI firewall tool. So you will be asked to enter your password. After doing this and entering the password, you can see a window like the one below:
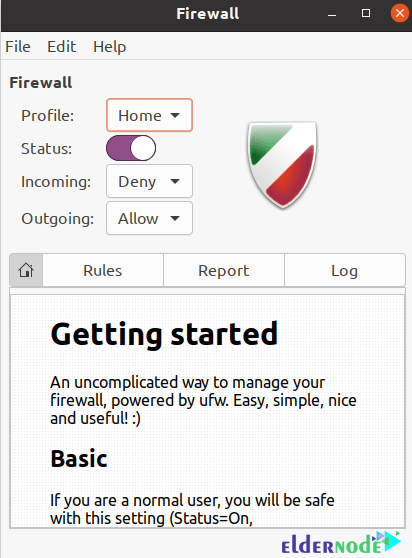
After viewing the image above, you must click on the Rules tab and then the + symbol at the bottom of the page. In the next step, you need to type “SSH” in the Application filter box and click on the orange icon:
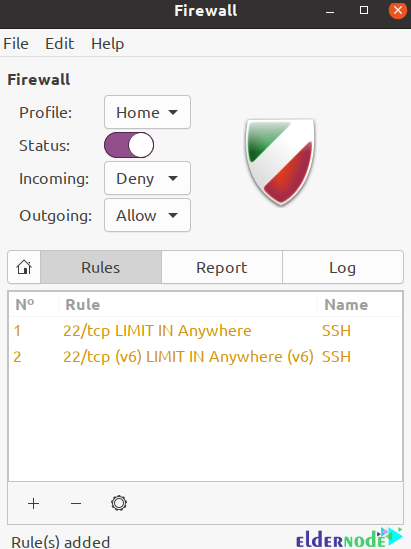
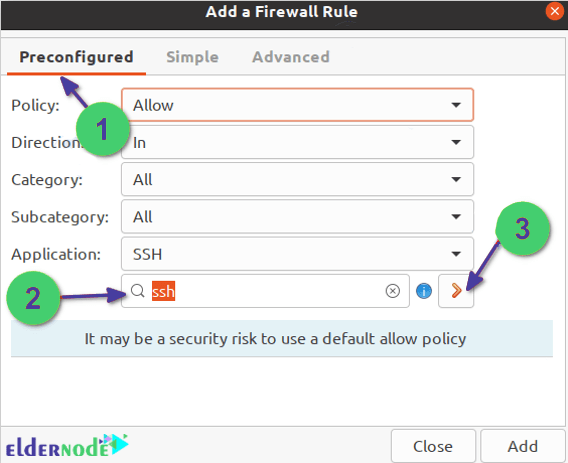
After viewing the image below and making sure to limit the policy, you can click “Add” and then the “Close” button:
Conclusion
In virtual and dedicated servers, one of the most effective ways to increase server security is to control the traffic and inbound and outbound connections of the server with the help of a firewall. This is done by setting up a firewall and blocking or restricting a service port or traffic. In Ubuntu 20.04 it can be done with a UFW firewall, so in this article, we tried to teach you How to Limit SSH with UFW on Ubuntu 20.04. You can also refer to the articles How to set up a Firewall with UFW on Debian 10 and Ubuntu 20.04.




