
DVWA web application aims to help security professionals and in order to measure their skills, help web developers to better understand the process of securing web applications. This article will explain 5 Reasons Why You Should Learn DVWA On Kali Linux. Eldernode website offers economical Linux VPS servers, which can be the best choice if you want to buy.
Table of Contents
Why You Should Learn DVWA On Kali Linux?
Damn Vulnerable Web Application or DVWA is an open-source and free damn vulnerable web application that is coded in PHP and uses MySQL database. It allows you to practice some of the most common web vulnerabilities at different levels of difficulty. Web developers can have a better understanding of how to secure web applications, and students and teachers can also learn all about web application security and potential vulnerabilities using DVWA.
1- Easy to Install and Use
DVWA is designed for security professionals eager to uncover and exploit some of the most common vulnerabilities of web platforms. You can install DVWA on Kali Linux using just a few lines of code. All you have to do is download DVWA, set up its prerequisites, which are Apache, PHP, and MySQL, and access DVWA from your browser.
2- Different Security Levels
DVWA has many web vulnerabilities, each vulnerability has four different security levels, which are low, medium, high and impossible. These security levels present a challenge to the attacker and also show how to counter any vulnerability with secure coding. Each level of security demands different skills:
–> High-Level Security: It is a kind of Zero Day environment and is the safe considered level.
–> Medium-Level Security: It includes all entry-level validations and filtration which can stop any script kiddie to get the benefit of available vulnerabilities.
–> Low-Level Security: It allows you to exploit all known vulnerabilities and try all attacks. That means there will be no security in a given framework.
–> Impossible: It is the default security level for DVWA and does not exhibit any vulnerabilities.
3- Weak Session IDs Attack
Damn Vulnerable Web Application can test the vulnerability of Weak Session IDs attacks. Users with weak Session IDs are exposed to having their session hijacked. Your session IDs should be unguessable so that your authentication scheme cannot be bypassed with relatively simple scripts. In fact, if the random generation algorithm is not secure, the attacker has the possibility to narrow down the range of values needed in an enumeration attack.
4- Command Injection Attack
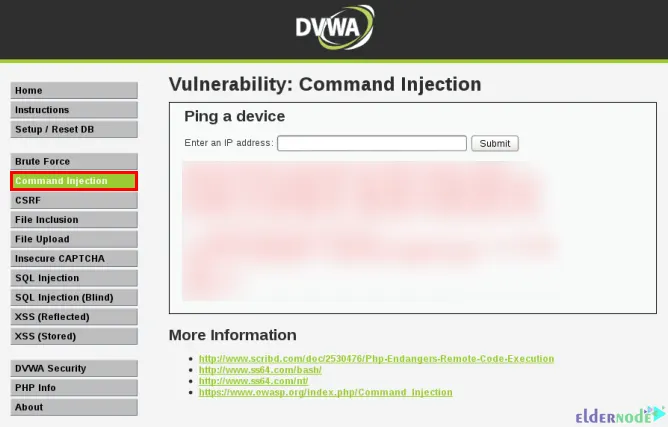
Command injection is an attack in which an attacker can input malicious command and run it on a target. This attack occurs when the attacker injects a malicious command into the target, and the web server executes the command. So, the ability to execute the command allows the attacker to steal information or install a malicious program, which can lead to an increase in the severity of the attack. DVWA can detect this attack. You can do this from the Command Injection tab on the DVWA home page:
5- CSRF Attack
One of the best options of DVWA is its ability to test the vulnerability of CSRF attacks. Cross-Site Request Forgery, or CSRF, is a web vulnerability that an attacker can use to trick users into taking actions they didn’t intend to. So, this vulnerability allows an attacker to partially bypass the SOP policy. The SOP policy is designed to prevent data theft by sending cross-origin requests.
Conclusion
DVWA has a simple interface and allows you to practice some of the most common web vulnerabilities, with different difficulty levels. In this article, we explained 5 reasons why you should learn DVWA on Kali Linux. I hope this tutorial was useful for you and it helps you to find reasons why to learn DVWA on Kali Linux. If you have any questions or suggestions, you can contact us in the Comments section.




