Stealth scan or Half-open scan is one of the scanning methods in Nmap in which the intruder uses to bypass the firewall and authentication mechanisms. Also, by using this method, they make the scan operation as normal network traffic and thus the scan is hidden. Due to the fact that the ACK packet is not sent by the attacker to the target system, the connection is not fully established. In some systems where complete communication is recorded, this type of scan can be used to prevent communication from being recorded in the target system. In this article, we are going to teach you How to Scan ports using Stealth Scan on Nmap. You can visit the packages available in Eldernode if you wish to purchase a VPS server.
Table of Contents
Tutorial Scan ports using Stealth Scan on Nmap
Stealth Scan is also known as SYN Scan or TCP SYN Scan because it sends only one SYN packet in the TCP Handshake process. This speed of operation and lack of communication is good for the scanner to prevent traffic analysis. Because there is no complete connection that anyone wants to analyze.
The TCP Three-Way Handshake process is implementing in the Stealth Scan, but in the last step of the Handshake, instead of confirming the connection, it sends an RST scanner and resets the connection to prevent further steps.
The general process of this type of scan is that first, the scanner sends a single data packet as SYN to the server, which is sent to the desired port that we want to scan.
After receiving the SYN packet, the server sends an SYN//ACK packet to the scanner if it provides a service on the port. That is, it is ready to communicate and the desired port is open.
Instead of sending an ACK to the server, the scanner then sends an RST to it. Then, it closes the connection there. But if the server sends RST in return, it means that the desired port on the server is Closed. This type of scan can use on almost all operating systems.
In the continuation of this article, join us to acquaint you with how to scan ports using Stealth Scan on Nmap.
Why should we scan ports?
Port scanning is an effective way to find vulnerabilities in a system. A port scan can tell an attacker (hacker) which ports are open in the system. This will help him find a way to attack your server. For example, if an attacker notices a “Secure Shell” server while listening to your port 22, it can try to obtain your weak passwords. If another server is running on another port, an attacker could log in and look for a bug to infiltrate. For example, it may be an older version of running software that has a known security hole.
In addition, these scans can use to find services that run on ports other than their default ports. For example, if you run an SSH server on port 65001 instead of port 22, port scanning can detect this. So the attacker, knowing this, tries to connect to your SSH server on that port. You can not just change the default ports and assume that your system is completely secure, although this makes it a little harder to find your server.
Port scanning is not only using by hackers. This is a very practical way to find security issues. For example, an organization can scan its own systems and identify its services that are visible, and find a way to secure them.
What is the Stealth?
In this type of scan, also known as stealth scan, only a TCP frame is sent to a port. No additional TCP Handshaking process or additional Packet transfer information is sent in this type of scan and only a Single Frame is sent to the target to analyze the response given.
As in this type of scan, a frame is sent, expecting to receive only one frame from the destination. Another name for this type of scan is the Half-Open Scan! This means that the TCP Handshake process is not complete in this type of scan. A session that has not yet been completed will be terminated as soon as a port is detected.
Scan ports using Stealth Scan on Nmap step by step
In this section, we want to introduce you to Scan ports using Stealth Scan on Nmap. It should be noted that Nmap has an option that simplifies and streamlines the process of performing TCP stealth scans. You can easily use the -sS command to perform TCP stealth scans with Nmap. Note that in the following command you must enter the IP address of the host you want to scan:
nmap -sS -P0 Your_IP_AddressThe output of the above command will be as follows:
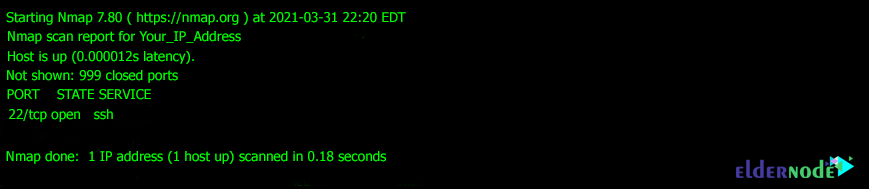
As you can see in the box above, the scan is performed. The output is that 999 ports are closed but port 22 is open.
Conclusion
In Stealth scanning, messages are sent with flag syn, which responds with syn/ack if the port is open. But if the port is closed, RST responds. This type of scan is using to bypass firewalls and authentication mechanisms. In this article, we tried to teach you How to Scan ports using Stealth Scan on Nmap.




