
SCTP scan is a tool to scan SCTP-enabled machines, under the EGPLv2 License that is used in high-performance networks. SCTP is part of the SIGTRAN protocol family that is used to carry SS7 over TCP/IP among other things. Using an SCTP scan allows you to find entry points to Telecom networks. You will need it when doing Pentests on Telecom Core Network infrastructures. In this article, you will learn How To Scan Ports With SCTP On Nmap. Order your considered package on Eldernode to have your own Linux VPS.
Table of Contents
Tutorial Scan Ports With SCTP On Nmap step by step
You are familiar with Nmap. It is a free and open-source tool for network scanning. SCTP is getting adopted quite fast at least for the SCTP stack. There is plenty of Open-source implementation of SCTP stack such as Linux and BSD with the KAME project. Scanning is an art that experts try to understand scan techniques and choose the appropriate one for a given task. Supported and tested environment for SCTP scan as host and port scanner are Linux and Mac OS X. Most of the scan types are only available to privileged users. This is because they send and receive raw packets, which requires root access on Unix systems. However, Scanning port using connect scan on Nmap and Scan port with the unprivileged user on Nmap was taught to you. Current Nmap releases have complete SCTP support. By default, Nmap performs an SYN Scan, though it substitutes a connect scan if the user does not have proper privileges to send raw packets (requires root access on Unix). In the following, you will learn about SCTP and scanning port with this on Nmap.
What is SCTP INIT Scan?
SCTP is an alternative to the TCP and UDP protocols, combining most characteristics of TCP and UDP, and also adding new features like multi-homing and multi-streaming. It is the SCTP equivalent of a TCP SYN scan. It is able to scan thousands of ports per second on a fast network not hampered by restrictive firewalls. Like SYN scan, INIT scan is relatively unobtrusive and stealthy, since it never completes SCTP associations. It also allows clear, reliable differentiation between the open, closed, and filtered states.
Since you don’t open a full SCTP association, this technique is known as half-open scanning. You send an INIT chunk as if you are going to open a real association and then wait for a response.
There is lots of room for improvement in the SCTP scan. Let’s review some of them:
– Complete implementation using libpcap
– Identification of scan response packet
– Better parameter cheching
SCTP Scanning and its Applications
SCTP is organized with TCP or UDP ports and the address space of SCTP ports is 16 bits and 65536 ports (from 0 to 65535). The main goal of the SCTP scan is to find SCTP live machines and open ports. SCTP scan embeds a list of common SCTP ports in order to find them by not scanning the 65535 ports but not a smaller subset. SCTP scan enables you to do many things such as:
1- Scan a single port on a machine
2- Scan whole A, B, C networks for machines with SCTP stacks
3- Scan for frequent ports on individual machine or whole networks
4- fuzz CTP stacks on one host
5- Port scan a host for the whole 65535 ports
6- Start a dummy server that binds socket 1000 which can be later scanned
Also, there is some handy option that enables SCTP scan to automatically portscan a machine as soon as it finds that this host actually supports SCTP.
Scan Ports With SCTP On Nmap
You can use SCTP packets to determine if a host is online by sending SCTP INIT packets and looking for ABORT or INIT ACK responses. This technique is named SCTP INIT ping scan that is implemented by Nmap.
However, to scan a port with SCTP, first, open your terminal and run:
nmap -sn -PY <target>Then, you can view the output that is the same format as the other types of ping scans:
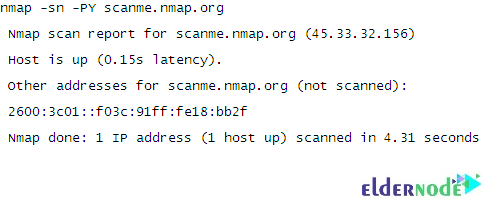
You should view the output as shown in the above image. The arguments -sn -PY scanme.nmap.org tell Nmap to scan an SCTP INIT going scan against the host scanme.nmap.org to determine if it is online.
Conclusion
In this article, you learned How To Scan Ports With SCTP On Nmap. SCTP scan allows you to examine networks. By default, results of the scan are sent to a central collaborative platform to help you make statistics on port usage and version usage.




