
Armitage is a framework for penetration testing that allows you to manage your penetration testing process and do it in the best possible way. This tool is a graphical version of metasploit that has a more user-friendly environment. Armitage is a very powerful and popular tool for security professionals and, of course, for novices, which has various exploits. In this article, we are trying to teach you How to install Armitage on Debian 10. You can visit the packages available in Eldernode if you need to buy Linux VPS server.
Table of Contents
Tuorial how to install Armitage on Debian 10
What are the uses of Armitage?
– Use in web penetration testing
– Ability to use in penetration testing on web servers and personal systems
– More than 500 functional payloads
– Easy to use and user friendly graphics
Learn How to install Armitage on Debian 10
Armitage is a great graphical user interface for metasplit. This tool was written by Raphael Mudge. Join us in the continuation of this tutorial to teach you how to install Armitage in Debian 10.
In the first step, you must use the following command to download and install Armitage in Debian 10:
apt-get install armitageAfter entering and executing the above command, Armitage is successfully installed. You must make sure that the postgresql database is running before you can run Armitage.
Note: If you wish, you can refer to the article on How to install PostgreSQL Database in Debian 10.
Start the database using the following command:
service postgresql startYou must enter the following command if you get a missing database.yml error:
service metasploit startIt should be noted that Armitage does not use the Metasploit service. But once it starts, the database.yml file will be launched for your system. Therefore, it is necessary to do this to execute Armitage.
# armitageAfter executing the Armitage command, a window like the one below will appear. Click on the connect to enter the next step:
In the next step you will be asked if you want Metasploit’s RPC server to start? Click Yes:
As you can see in the image below, the progress bar starts:
The main environment of the Armitage program
You will now be taken to the main environment of the Armitage program. Like the image below:
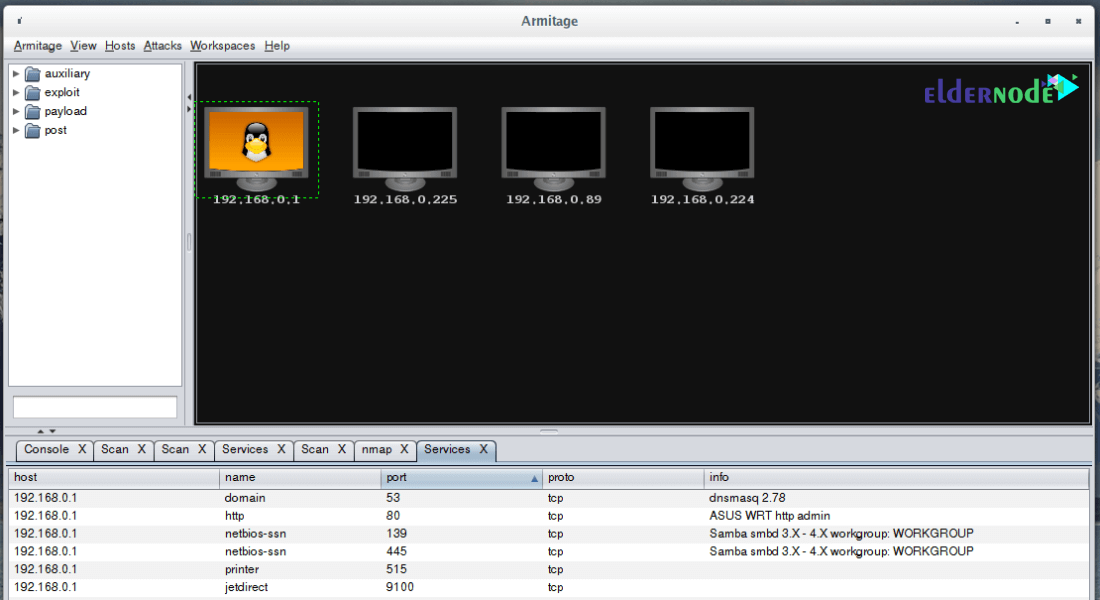
In the toolbar at the top of the program there are options, the applications of which are as follows:
Armitage item: In this section you can control how to connect to the application server and settings related to the graphical display or table of existing targets.
View item: In this section, you can add console items, credentials, downloads, jobs, loot, script console, or background tasks, and add reports to the application environment if needed.
Host item: In this section, if you have saved the IP number or target address in Notepad, you can call the Armitage environment via the Import Hosts option. Or you can manually enter the target IP through the second Add Hosts option.
Another feature of reinforcement is the use of Nmap tools. You can use different scans to identify your target by clicking on Nmap Scan. You can also use the program’s own tool (MSF Scans) to scan the victim target.
Attacks item: If you have defined the target IP or address in the application environment, Armitage has the power to automatically search for the right exploits for your target.
Introducing various tools of Armitage program
Well now we go to the toolbar on the left side of the program which contains the auxilliary library, exploit, payload, post.
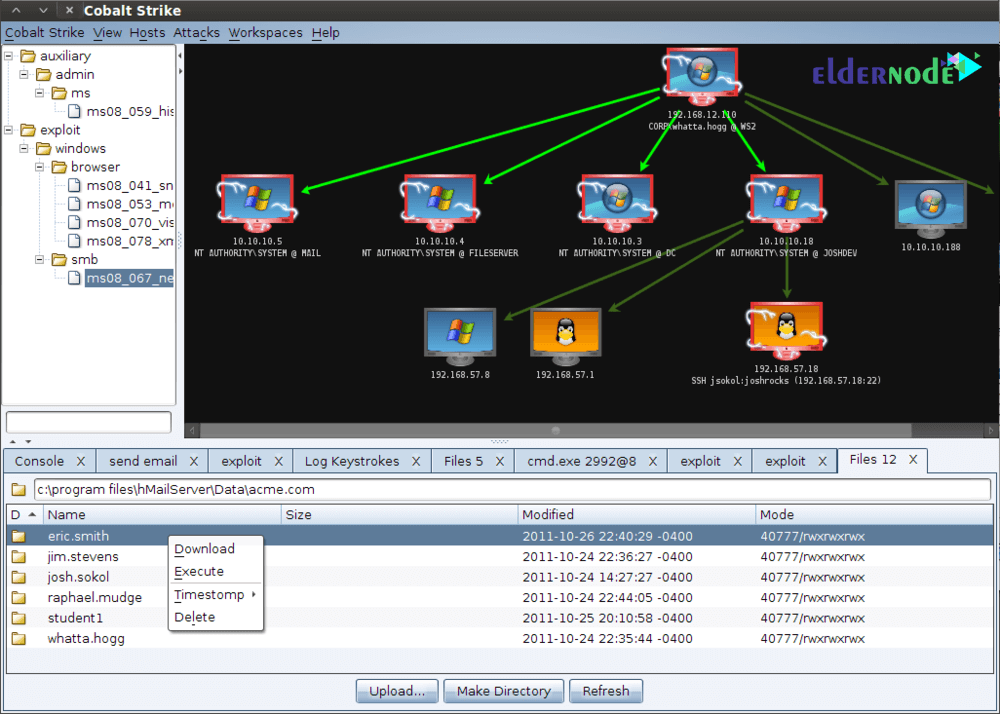
Auxilliary folder: In this library you will see a list of all auxiliary variables of modules with metasploit.
Metasploit folder: In this library, you will see a list of all exploits in the Armitage program. In this section, how to penetrate the target, which depends on the parameters of the operating system type, open ports, firewalls, etc. by selecting Exploit Properly formed.
Payload folder: In this library you will see a list of all payloads in Armitage. For example, after the intrusion, you want to get a series of controls on the target side (such as access to the command line, FTP, database, etc.) that with this library you will be able to do your operation.
Post folder: Used to send exploit modules to a specific target server with different applications.
Note: In the left bar of the program, you will see the list of target IPs that you introduced to Armitage. Also in the bottom toolbar, the main program environment is used for scanning and exploitation operations.
Conclusion
Armitage is a framework for penetration testing that allows you to manage the penetration testing process and do it in the best possible way. In fact, Armitage integrates your metasploit penetration test and meets the needs of different tools for different stages of penetration testing. In this article, we tried to teach you How to install Armitage on Debian 10 and also explain its various tools.




